Of course other wiser people spend much more time on this topic, but reinventing the wheel is quite fun, and nothing is more educating. And perhaps it will help you understand the problem of security a bit better.
Dictionary Hack
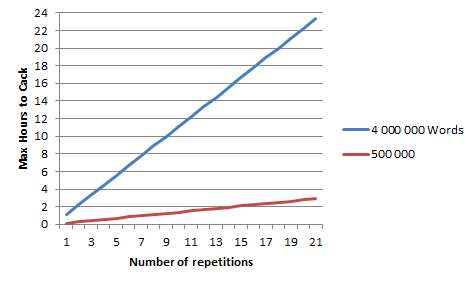
I assumed a cracking speed of 1000 guesses/second, and assumed a dictionary crack (i.e. simply trying out words in a predefined list and comparing the resulting hash to the target hash).If you take a list of 4 million words (perhaps words used 99% in languages based on the latin alphabet), then testing each word in the list takes a total of:
4 000 000 / 1000 (seconds) => /60 (minutes) => /60 (hours) => /24 (days)
= ~1h 07
... around 1 hour and 7 minutes.
If you try repeating the words, say twice in a row, you now have 4 million extra words to test, each being the double a word from the original list.
Repeat three times, you have another 4 million rows.
... this makes for a nice linear progression;
So if you take a random word, say "closet", and repeat it 9 times: "closetclosetclosetclosetclosetclosetclosetclosetcloset" as you password, it would only take 8 hours to hack your password.
If you take more realistically, only half a million words, the password above would be discovered in 1 hour 30 minutes. (I would have taken less honestly, but the red line would hug the bottom axis and no relevant progression could be seen. So just imagine that for a realistic amount, only perhaps 5000 commonly used words which includes words you use for your password, hacking your password would be as fast as it takes you to click a mouse button).
Brute Force
Now if you just use random letters, numbers and symbols, your password could be: "A!diT0la%"Brute Force works by trying out every possible character combination for a certain set of characters
So if you use all small letters [a-z] (26), capital letters [A-Z] (26), digits [0-9] (10), and some special signs [!"§$%&/()=?*'#+~] (16), for every possible character in your password, you have a total of (26+26+10+16 = 78) characters to chose from.
So for 1 letter passwords, you can try a maximum of 78 times before guessing the password.
At 2 letters it is already 78*78, because every character can be combined with itself and all other characters in the list, which makes for 6084 maximum guesses.
... this is exponential growth:
Already at a password length of 4 characters (ex. "$jO9") it takes 10 hours to go through all possibilities. If you just use 6 random lowercase letters [a-z] (ex. "lbocca") it takes ~85 hours (3.5 days) to try all possible guesses. Using 6 random characters with 78 options (ex. "§klOD&"), it takes 801 hours (~1 Month) to go through all options.
Randomness
Yes, the longer the password you use, the longer is the maximum time it takes for it to get cracked.but "closetclosetclosetclosetclosetclosetclosetclosetcloset" is not as secure as "§klOD&"!
This is due to randomness(!) - the more predictable you are, the easier it will be to exploit you.
And using known words "closet" is more predictable than using random characters "§klOD&". And for a computer to check if you used "closet" 9-times in a row, or with a 1 at the end, really isn't that much more of a trouble.
So the goal when attempting to create security, is to be random enough to fool potential attackers, but organised enough to be able to remember your own password. (Try remembering "!9dA85Dso§d" ;)
This demonstrates beautifully, that Security is always a matter of finding a balance between usability(can i remember my password?) and risk attitude (how ok is it if my password gets cracked?).
Update: here a link to some other opinions on word repetition in a password.

No comments:
Post a Comment